Kubernetes 1.29使用群辉dsm7 NFS存储创建StorageClass持久化
- 系统运维
- 2025-08-01
- 76热度
- 0评论
目前单机创建NFS服务器高可用数据不好实现,使用CEPH数据存储又可能比较麻烦,还需要额外维护单独CEPH集群,本次采用群辉NFS存储进行模拟测试
群辉配置
登录群辉,需要搭建可以参考下面的文章
开启NFS Server服务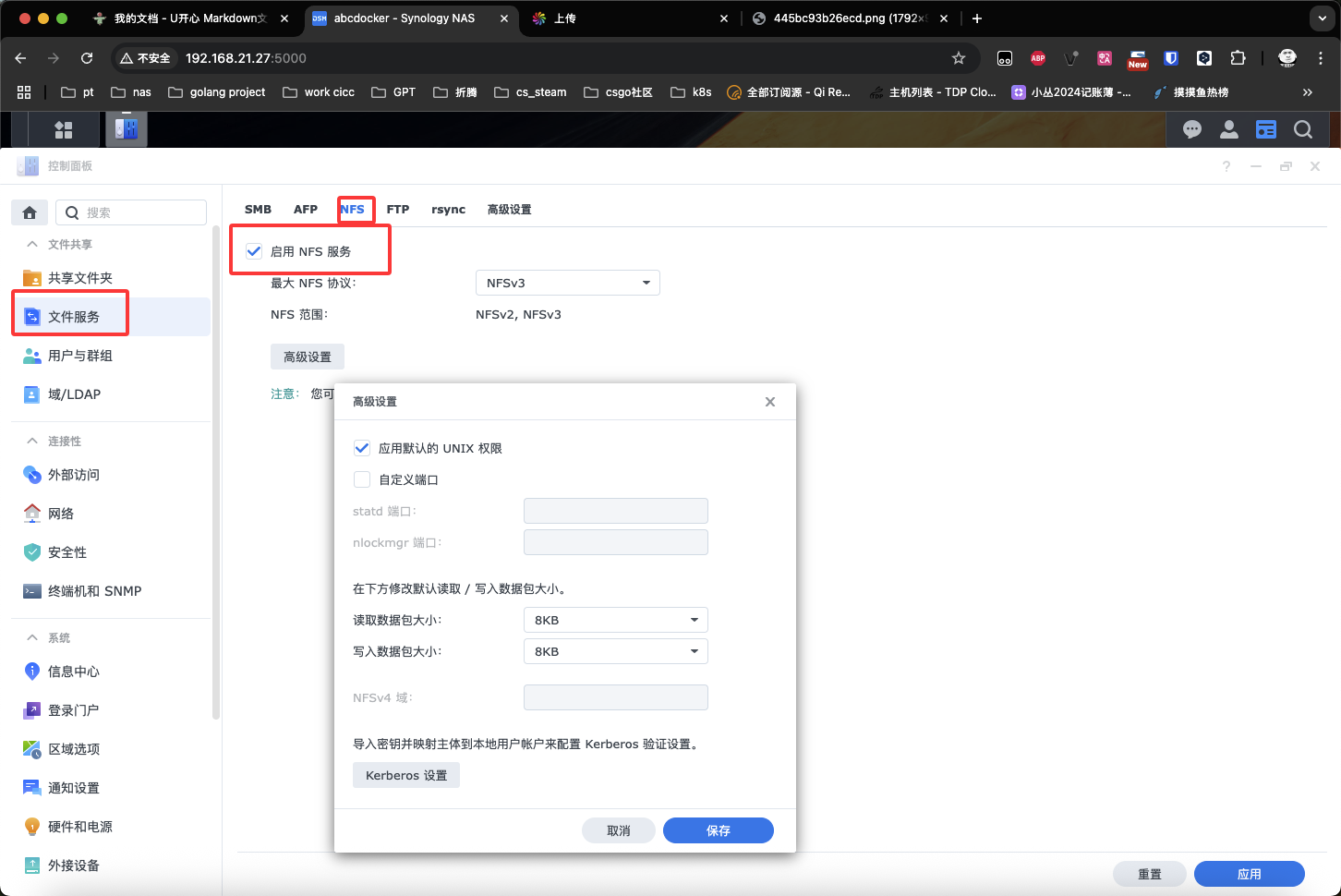
创建共享目录,打开控制面板
创建共享目录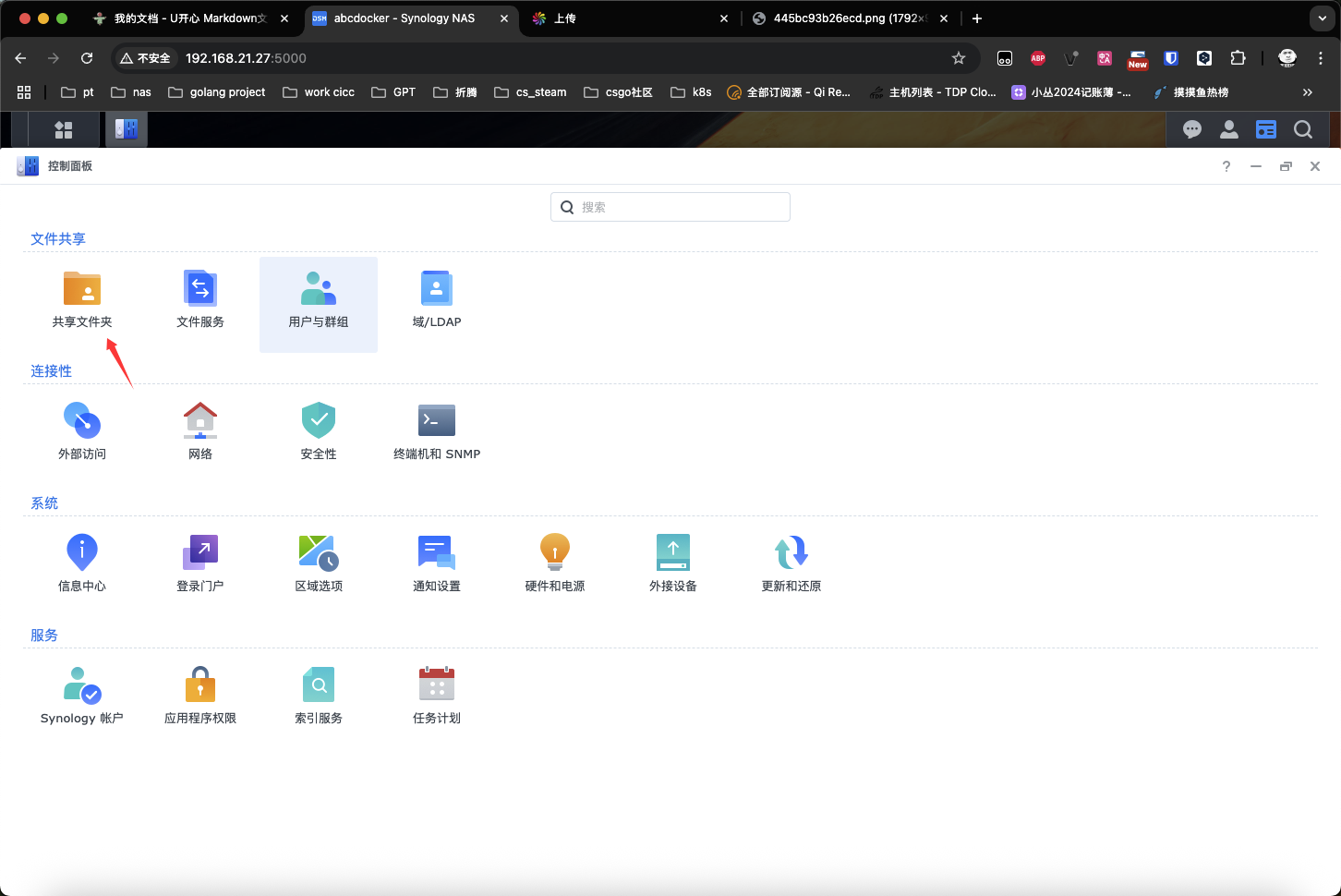
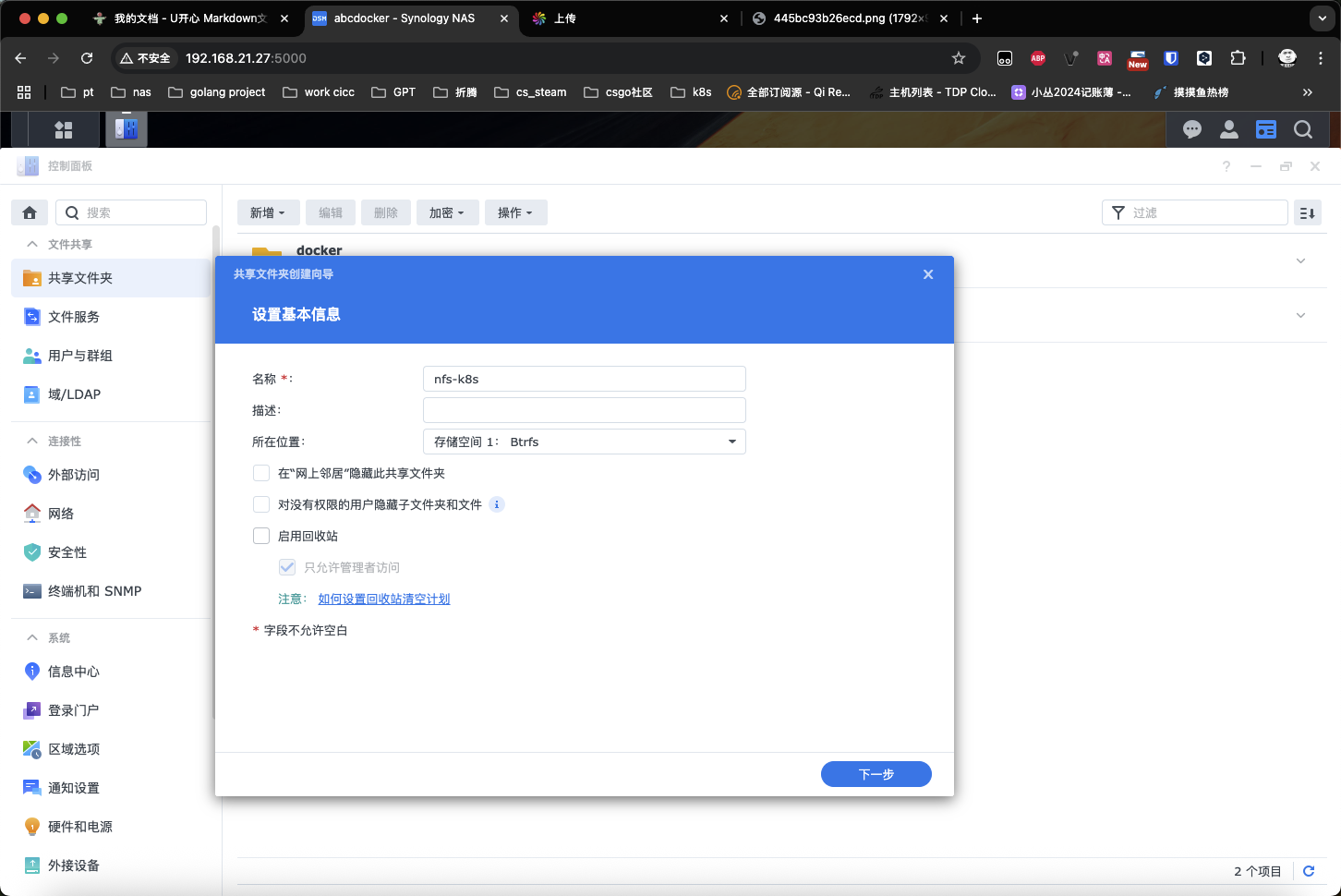
设置目录名称nfs-k8s
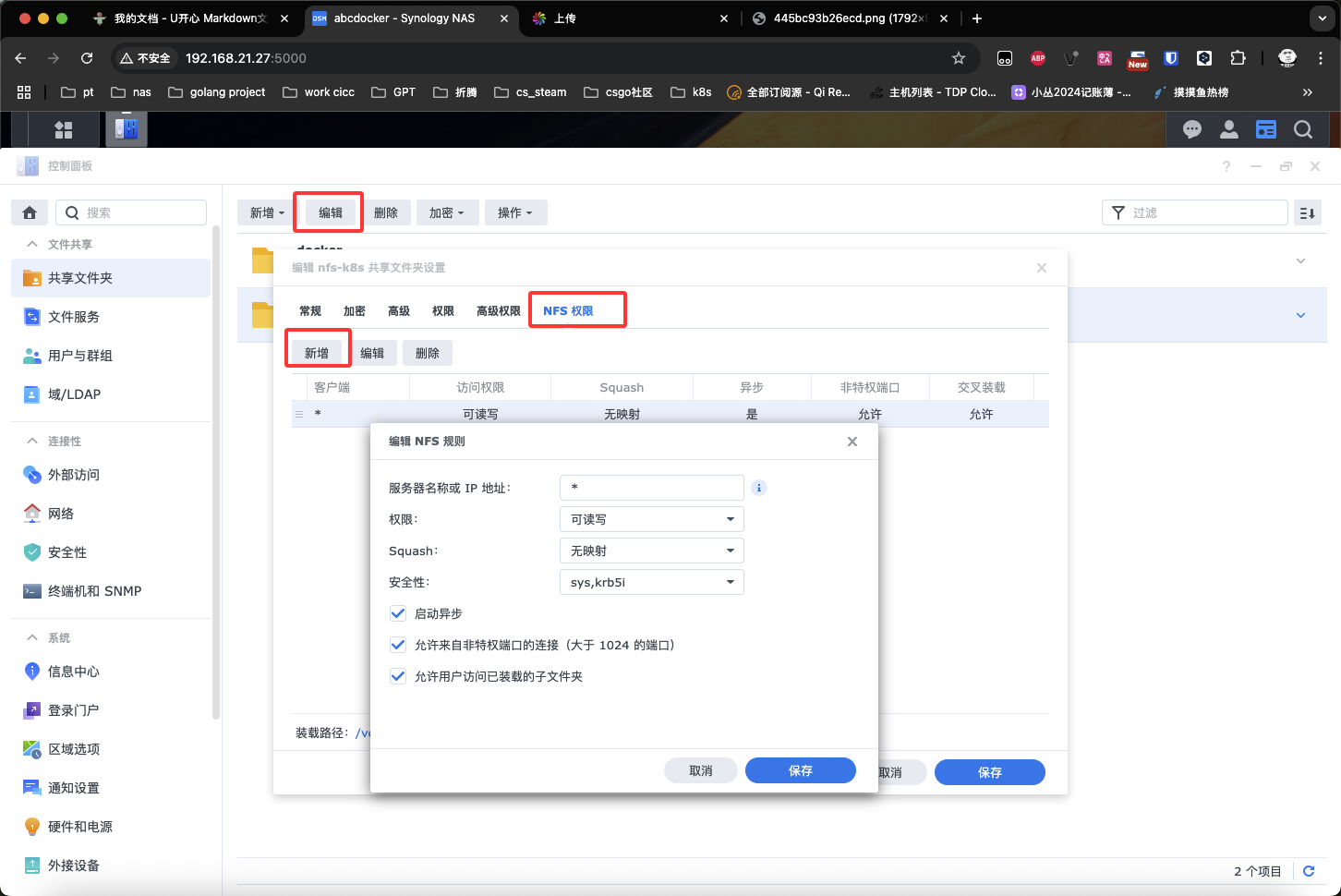
按照下面的配置,设置NFS Server权限
开启File Station 匿名用户访问权限
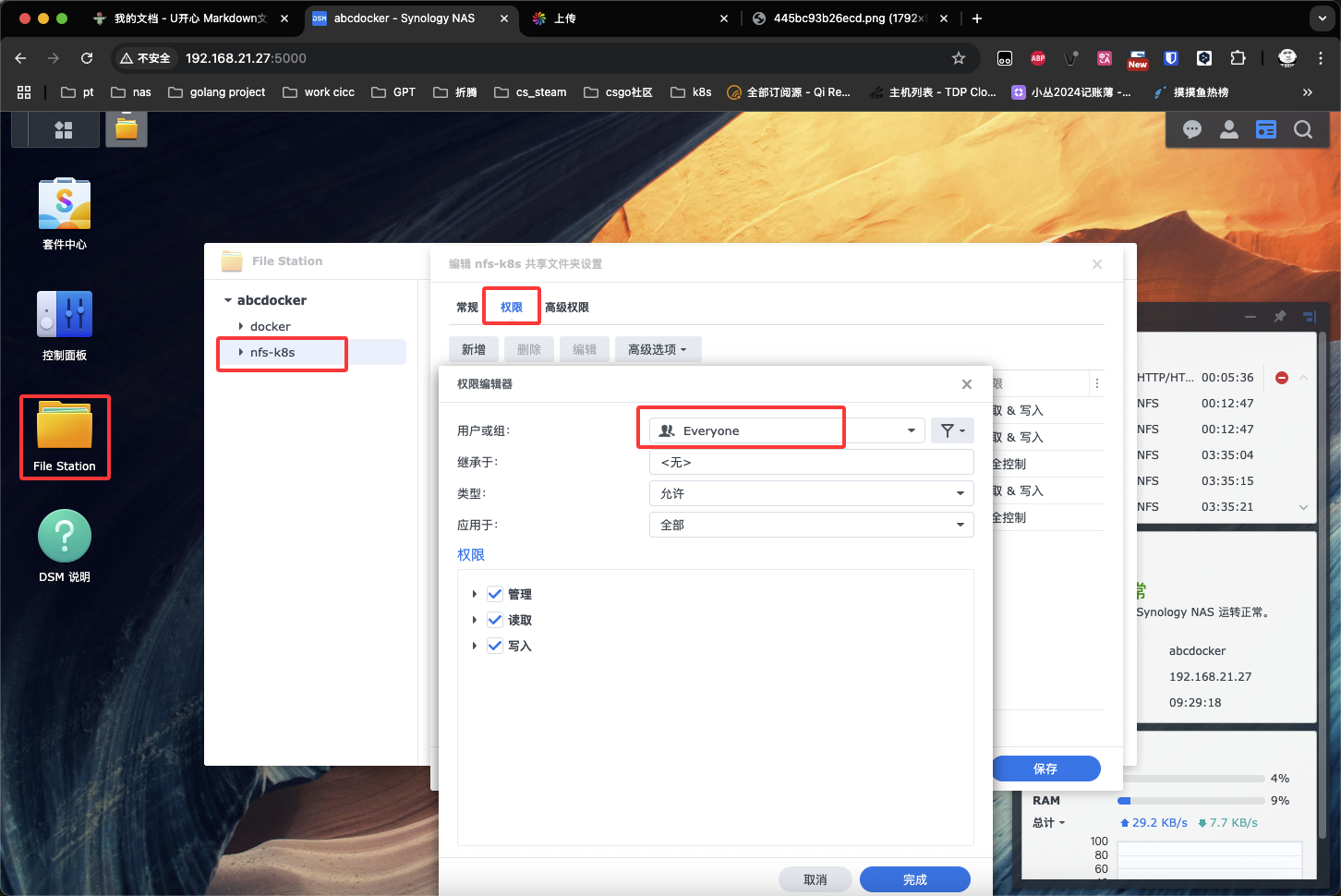
挂载目录可以在共享目录中看到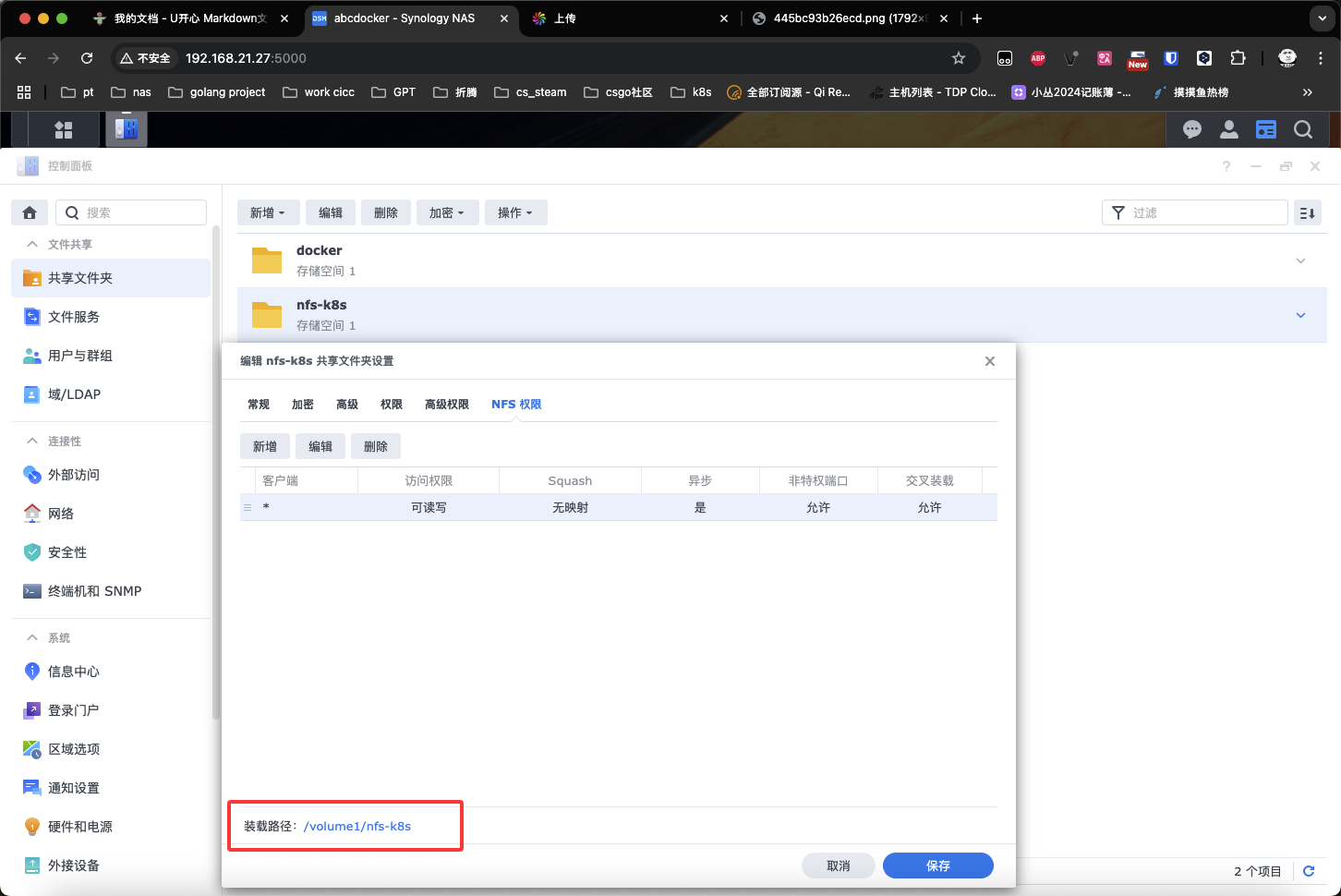
Kubernetes 存储卷创建
- 所有k8s节点安装nfs (我这里以Ubuntu为例)
sudo apt updatesudo apt install nfs-kernel-server
执行showmount测试nfs挂载情况
root@k8s-master-01:~# showmount -e 192.168.21.27Export list for 192.168.21.27:/volume1/nfs-k8s *root@k8s-master-01:~#
接下来为nfs创建rbac权限
apiVersion: v1kind: ServiceAccountmetadata:name: nfs-client-provisioner# replace with namespace where provisioner is deployednamespace: default---kind: ClusterRoleapiVersion: rbac.authorization.k8s.io/v1metadata:name: nfs-client-provisioner-runnerrules:- apiGroups: [""]resources: ["nodes"]verbs: ["get", "list", "watch"]- apiGroups: [""]resources: ["persistentvolumes"]verbs: ["get", "list", "watch", "create", "delete"]- apiGroups: [""]resources: ["persistentvolumeclaims"]verbs: ["get", "list", "watch", "update"]- apiGroups: ["storage.k8s.io"]resources: ["storageclasses"]verbs: ["get", "list", "watch"]- apiGroups: [""]resources: ["events"]verbs: ["create", "update", "patch"]---kind: ClusterRoleBindingapiVersion: rbac.authorization.k8s.io/v1metadata:name: run-nfs-client-provisionersubjects:- kind: ServiceAccountname: nfs-client-provisioner# replace with namespace where provisioner is deployednamespace: defaultroleRef:kind: ClusterRolename: nfs-client-provisioner-runnerapiGroup: rbac.authorization.k8s.io---kind: RoleapiVersion: rbac.authorization.k8s.io/v1metadata:name: leader-locking-nfs-client-provisioner# replace with namespace where provisioner is deployednamespace: defaultrules:- apiGroups: [""]resources: ["endpoints"]verbs: ["get", "list", "watch", "create", "update", "patch"]---kind: RoleBindingapiVersion: rbac.authorization.k8s.io/v1metadata:name: leader-locking-nfs-client-provisioner# replace with namespace where provisioner is deployednamespace: defaultsubjects:- kind: ServiceAccountname: nfs-client-provisioner# replace with namespace where provisioner is deployednamespace: defaultroleRef:kind: Rolename: leader-locking-nfs-client-provisionerapiGroup: rbac.authorization.k8s.io
创建Deployment
apiVersion: apps/v1kind: Deploymentmetadata:name: nfs-client-provisionerlabels:app: nfs-client-provisioner# replace with namespace where provisioner is deployednamespace: defaultspec:replicas: 1strategy:type: Recreateselector:matchLabels:app: nfs-client-provisionertemplate:metadata:labels:app: nfs-client-provisionerspec:serviceAccountName: nfs-client-provisionercontainers:- name: nfs-client-provisionerimage: dockerproxy.frps.fun/dyrnq/nfs-subdir-external-provisioner:v4.0.1volumeMounts:- name: nfs-client-rootmountPath: /persistentvolumesenv:- name: PROVISIONER_NAMEvalue: k8s-sigs.io/nfs-subdir-external-provisioner- name: NFS_SERVERvalue: 192.168.21.27- name: NFS_PATHvalue: /volume1/nfs-k8svolumes:- name: nfs-client-rootnfs:server: 192.168.21.27path: /volume1/nfs-k8s
我这里提供下面镜像
dockerproxy.frps.fun/dyrnq/nfs-subdir-external-provisioner:v4.0.1
官方默认镜像地址为dyrnq/nfs-subdir-external-provisioner:v4.0.1
这里是创建StorageClass
apiVersion: storage.k8s.io/v1kind: StorageClassmetadata:name: dsm7-nfs-clientprovisioner: k8s-sigs.io/nfs-subdir-external-provisioner # or choose another name, must match deployment's env PROVISIONER_NAME'parameters:archiveOnDelete: "false"
查看所有已创建的资源
root@k8s-master-01:~/nfs# kubectl get pod,sa,scNAME READY STATUS RESTARTS AGEpod/nfs-client-provisioner-594f79d67b-wvx5s 1/1 Running 0 23mNAME SECRETS AGEserviceaccount/default 0 22hserviceaccount/nfs-client-provisioner 0 26mNAME PROVISIONER RECLAIMPOLICY VOLUMEBINDINGMODE ALLOWVOLUMEEXPANSION AGEstorageclass.storage.k8s.io/dsm7-nfs-client k8s-sigs.io/nfs-subdir-external-provisioner Delete Immediate false 13s
将dsm7-nfs-client设置为默认storageclass
root@k8s-master-01:~/nfs# kubectl patch storageclass dsm7-nfs-client -p '{"metadata": {"annotations":{"storageclass.kubernetes.io/is-default-class":"true"}'
查看设置default状态
root@k8s-master-01:~/nfs# kubectl get scNAME PROVISIONER RECLAIMPOLICY VOLUMEBINDINGMODE ALLOWVOLUMEEXPANSION AGEdsm7-nfs-client (default) k8s-sigs.io/nfs-subdir-external-provisioner Delete Immediate false 5m
测试pvc如下
apiVersion: v1kind: PersistentVolumeClaimmetadata:namespace: defaultname: abcdocker-test-pvclabels: {}spec:accessModes:- ReadWriteManyresources:requests:storage: 10GistorageClassName: dsm7-nfs-client
这里提示已绑定,代表PVC验证完毕
root@k8s-master-01:~/nfs# kubectl apply -f test-pvc.yamlpersistentvolumeclaim/abcdocker-test-pvc createdroot@k8s-master-01:~/nfs# kubectl get pvcNAME STATUS VOLUME CAPACITY ACCESS MODES STORAGECLASS VOLUMEATTRIBUTESCLASS AGEabcdocker-test-pvc Bound pvc-ba81924e-3d04-4173-9abf-d17972f6fa5b 10Gi RWX dsm7-nfs-client <unset> 5s